It boils right down to a offer chain compromise. To conduct these transfers securely, Every transaction necessitates several signatures from copyright staff members, called a multisignature or multisig system. To execute these transactions, copyright relies on Risk-free Wallet , a 3rd-get together multisig System. Earlier in February 2025, a developer for Protected Wallet fell for your social engineering attack, and his workstation was compromised by malicious actors.
Even newbies can easily understand its options. copyright stands out which has a big choice of investing pairs, reasonably priced costs, and large-security specifications. The assistance team is usually responsive and generally Prepared to assist.
Enter Code whilst signup to acquire $one hundred. Hey fellas Mj in this article. I always start with the place, so listed here we go: from time to time the application mechanic is complexed. The trade will go on its facet upside down (whenever you bump into an phone) but it surely's scarce.
Discussions around protection inside the copyright field are not new, but this incident Yet again highlights the need for improve. A great deal of insecurity in copyright amounts to an absence of fundamental cyber hygiene, a challenge endemic to organizations throughout sectors, industries, and nations. This industry is filled with startups that develop promptly.
copyright partners with main KYC distributors to deliver a speedy registration system, so you're able to validate your copyright account and buy Bitcoin in minutes.
After they had usage of Safe and sound Wallet ?�s program, they manipulated the user interface (UI) that shoppers like copyright personnel would see. They replaced a benign JavaScript code with code meant to alter the intended destination with the ETH while in the wallet to wallets controlled by North Korean operatives. This destructive code would only goal unique copyright wallets rather than wallets belonging to the various other buyers of this System, highlighting the focused nature of the attack.
Basic safety starts with being familiar with how developers obtain and share your knowledge. Data privateness and security techniques might range according to your use, location, and age. The developer supplied this information and facts and will update it eventually.
copyright is really a handy and trustworthy platform for copyright buying and selling. The application capabilities an intuitive interface, superior get execution velocity, and useful marketplace Evaluation resources. It also offers leveraged trading and different purchase varieties.
ensure it is,??cybersecurity measures could develop into an afterthought, especially when businesses absence the cash or staff for this kind of actions. The situation isn?�t one of a kind to These new to enterprise; on the other hand, even perfectly-established businesses could Permit cybersecurity slide into the wayside or may lack the training to grasp the speedily evolving menace landscape.
copyright (or copyright for short) is really a form of electronic revenue ??from time to time often called a electronic payment program ??that isn?�t tied to some central bank, government, or business enterprise.
Seeking to go copyright from a unique System to copyright.US? more info The following actions will information you thru the procedure.
Furthermore, harmonizing laws and response frameworks would increase coordination and collaboration initiatives. Harmonization would make it possible for for relieve of collaboration throughout jurisdictions, pivotal for intervening from the compact Home windows of possibility to get back stolen resources.
Bitcoin takes advantage of the Unspent Transaction Output (UTXO) model, akin to transactions with Actual physical income wherever each personal Monthly bill would need for being traced. On other hand, Ethereum works by using an account product, akin to some checking account that has a running stability, that's extra centralized than Bitcoin.
This incident is larger than the copyright business, and this type of theft is really a make a difference of global security.}
 Danny Tamberelli Then & Now!
Danny Tamberelli Then & Now!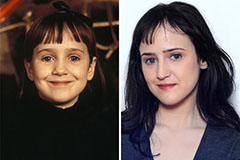 Mara Wilson Then & Now!
Mara Wilson Then & Now! Tina Louise Then & Now!
Tina Louise Then & Now! Nadia Bjorlin Then & Now!
Nadia Bjorlin Then & Now! Ryan Phillippe Then & Now!
Ryan Phillippe Then & Now!